Modern web applications typically need a strong security footprint with a seamless login flow, including ASP.NET Core apps. Earning the trust of your customers and users requires nothing less. Your application needs to leverage the OpenID Connect (OIDC) and OAuth 2.0 standards for a secure user authentication approach. It provides the best way to offer users a superior ASP.NET authentication experience.
Duende IdentityServer supports OIDC and OAuth 2.0, while letting you fully control your ASP.NET Core app’s User Experience (UX) and business logic. It easily supports building a user interface and login flow that matches the requirements of your app design. Use your own authentication approach (MFA, passwords, biometrics), your own database, or even federated logins from other providers.
IdentityServer streamlines the process of incorporating state-of-the-art identity and access management functionality into ASP.NET Core projects. This includes crafting a login flow that provides seamless and secure access to your applications. Let’s take a closer look at this effort, illustrating how easy securing your company’s apps becomes with Duende.
Designing an Effective Login Flow
Any effective login flow starts with a simple and intuitive design. After all, this form serves as the front door for your web application. The same concept applies to other pages within this flow, such as those for password reset or user registration.
IdentityServer’s built-in support for OIDC and OAuth 2.0 ensures your app also has industry-standard identity and access management functionality. It seamlessly supports ASP.NET Identity, or you can also use another identity library or a custom database solution. You gain the flexibility to build a login flow that fully meets your specifications.
How the Login Page Interacts with the Authorization Endpoint
When a user needs to log in to your ASP.NET Core application, it redirects the user to the authorization endpoint. This endpoint is typically located on the server running IdentityServer. This authorization request process ultimately displays the login page of your application.
After successfully authenticating the user, IdentityServer redirects them to the page issuing the authentication challenge. This is typically defined in the returnURL. A failed authentication redirects the user to the login form or another page of your choosing. Note that this authentication session is managed with ASP.NET Core’s built-in authentication framework that utilizes cookies. Understanding this framework is critical when designing your login pages and workflow.
For a better insight into how your application’s pages interact with the IdentityServer middleware, examine this diagram.
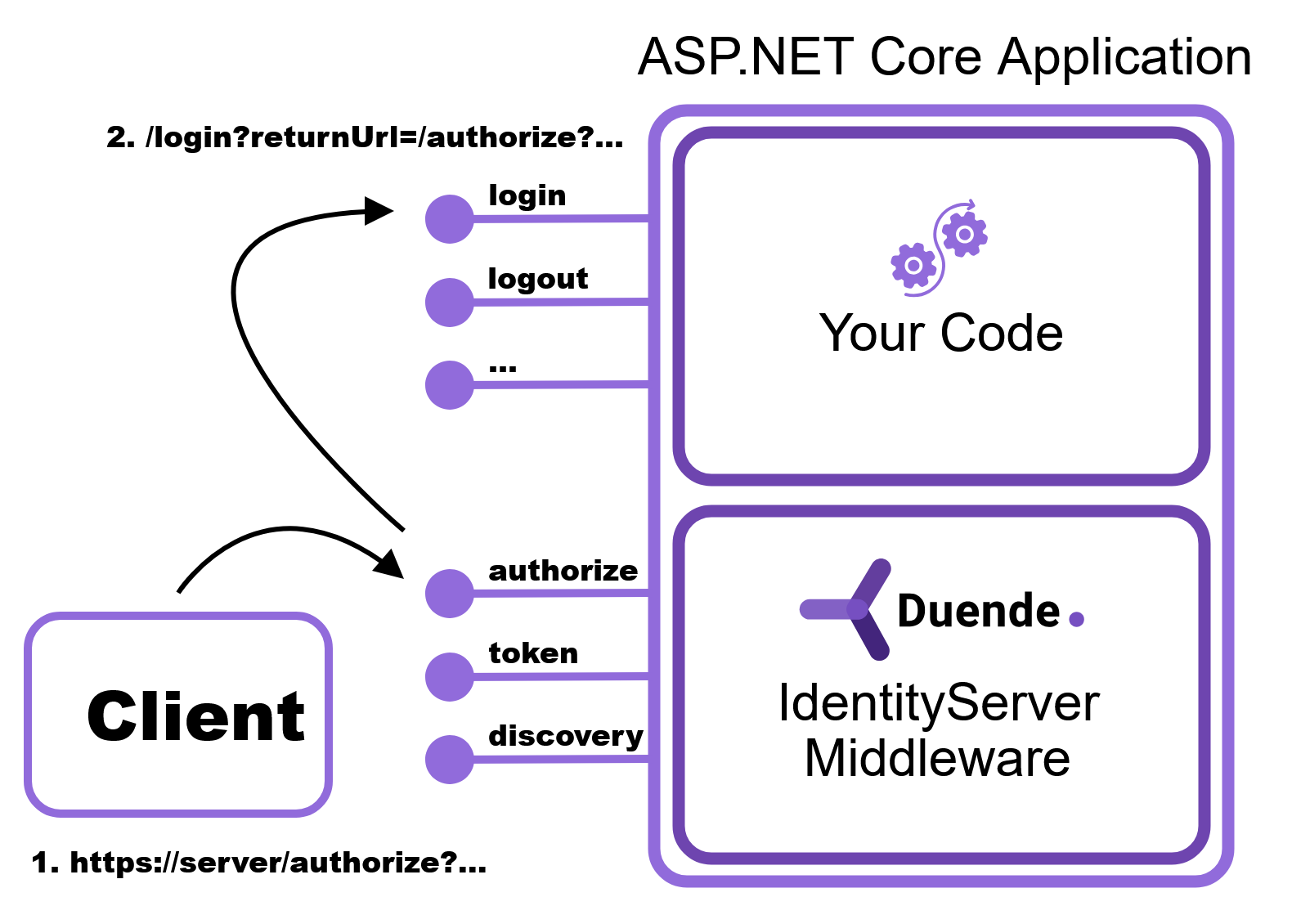
When receiving an authorization request, IdentityServer checks for an authentication session for the current user. When using ASP.NET authentication, that session is confirmed using a cookie generated by the successful login process. The lack of a cookie means the user in question is not currently logged in. As such, any request to the authorization endpoint results in the application redirecting the user to the login page.
This redirection serves as the entry point to the login workflow defined by your application. After successfully logging in, the next request sent to the authorization endpoint has an authentication cookie for that user. The IdentityServer middleware generates an appropriate protocol response, and the user gains access to the relevant application.
This example workflow illustrates how IdentityServer integrates seamlessly with your ASP.NET Core application for authentication purposes. You gain the benefits of an industry-standard authentication engine while maintaining control over your application and its UX. IdentityServer makes it easy to implement OIDC, ASP.NET Identity, and OAuth 2.0 with your ASP.NET Core apps.
Implement the Required Login Flow Pages
When implementing IdentityServer to provide OIDC support in your ASP.NET Core application, our middleware expects a few standard pages. When the web browser makes requests to the following endpoints, the user is redirected to these pages. Let’s examine each one:
- Login: The login page provides authentication functionality, including basic password entry or more esoteric methods. It even supports using an external authentication provider.
- Logout: A simple page allowing the user to log out of your application. Supporting single sign-out is also possible.
- Error: This page is used to display any errors encountered during the login flow or elsewhere within your application
- Consent (optional): The optional consent page is used when the user needs to allow the client access to certain resources. While this page is generally only used with third-party clients, it still must be implemented.
For more information on implementing these pages, along with sample code, check out the tutorial on building interactive applications. Additionally, here is a similar tutorial that uses ASP.NET Identity. Also, check out this tutorial, which uses the Duende IdentityServer UI Template.
Adding Other Functionality to the Login Flow
IdentityServer also supports other functionality related to the login process. Let’s explore some of these options. All told, they illustrate the ease of crafting a robust OIDC-compliant login flow when using our framework.
Supporting other authentication methods beyond the traditional ID/password entry becomes easy when using IdentityServer. This includes specialized options such as multi-factor authentication (MFA), knowledge-based authentication (KBA), and even passwordless authentication. If you need to require users to agree to your terms of service before logging in, that’s also possible.
Even more unique login scenarios are possible, including home-realm discovery, which facilitates the use of external authentication providers. IdentityServer even allows accounts to be reconciled across multiple user databases. Onboarding new users from other external providers also becomes easier with IdentityServer’s support for the OIDC standard.
Again, the UI and business logic used for these more complex login flows are separate from the IdentityServer library. This architectural approach lets your developers craft a custom login flow that seamlessly supports OpenID Connect and OAuth 2.0. Our engine implements the endpoints detailed in the OIDC specification, while your team writes the code supporting their functionality. IdentityServer effectively combines your business logic with the industry-leading standards for authentication and authorization.
Craft an Exceptional Login Experience with IdentityServer as your Middleware
If you want to build an ASP.NET Core application with a secure login flow, add IdentityServer to your project. We provide seamless support for OpenID Connect, ASP.NET Identity, and OAuth 2.0, while you control the user experience. Check out our comprehensive documentation for code examples and detailed explanations. Contact our sales team for more insights to help you make an informed decision on using our security framework.
