When building a modern web application, software architects must pay close attention to designing a strong cybersecurity footprint. After all, cybercriminals continue devising new techniques for surreptitiously accessing websites and stealing data. As a result, application developers need to be proactive in keeping unethical hackers out.
Any effective application security strategy involves utilizing modern authorization and authentication frameworks, like OAuth 2.0 and OpenID Connect (OIDC). The lifeblood of both of these standards is a small chunk of data known as a token. An encrypted token provides applications and APIs with information about a user and their access permissions. They play a key role in providing access to legitimate users while not allowing cybercriminals.
The two major token types are access tokens and identity tokens. Let's examine the important differences between both and how each is used within a modern web application architecture. Use this information to build web and mobile applications with stronger security footprints.
What is an Identity Token?
An identity (or ID) token is a small digital entity containing information about an authenticated application user. When a user logs in through a central identity provider (IdP), that process retrieves information about them. In addition to personal information, it also includes data about the authentication method, a timestamp, and a unique ID.
An OIDC-compliant IdP, like Duende IdentityServer, embeds this information in an encrypted identity token. This embedding process includes other data, such as an expiration timestamp, session ID, and more. The JSON Web Token (JWT) format is used for identity tokens, relying on a standard familiar to most modern developers.
Identity tokens are only used by the client application that initiated the original login. They include a nonce, which stands for "number only used once," as a unique ID to enforce this rule. Check out the OpenID Connect specification documentation for additional insights on identity tokens.
What is an Access Token?
Access tokens are virtual authorization tickets used for securing web applications and their APIs. They provide permission for users – either humans or other systems – to access an application and its underlying resources. Beyond APIs themselves, these resources might include a content delivery server, documentation, or even media.
Access tokens contain data identifying the client as well as token creation and expiration timestamps. Of special importance within the token are scopes, which define the access rights for the user. This data is stored as key-value pairs, known as claims, typically embedded within the JWT format.
What about Reference and Refresh Tokens?
Two other related tokens deserve mention. Used by an authorization server, reference tokens contain a unique ID that points to the data within the original access token. Finally, a refresh token is used to request new access tokens without requiring reauthentication, providing a superior user experience. Considering their power, special care must be taken in securing refresh tokens from surreptitious access!
The OAuth 2.0 specification documentation provides more details on access and refresh tokens.
Access Token vs. ID Token: The Critical Differences
After that overview of access tokens and identity tokens, let's now examine their relevant differences in web application architecture. Use these insights to design modern web (and mobile) applications that keep critical resources secure.
• Authorization vs. Authentication: The IdP provider issues an ID token used to identify an authenticated user. Some IdPs also generate an access token, which grants authorization to access an application's underlying resources. In short, proof of authorization = access token; proof of authentication = identity token.
• Token Format: Identity tokens leverage the JWT format. In fact, it's part of the OIDC specification. Most access tokens also use the JWT format, but reference tokens simply contain a unique ID.
• Accessing APIs: Applications only use access tokens for communicating with APIs and other app resources. Never try to connect to an API using an ID token.
• User Information: Only ID tokens have personal identifying information about a user, like name and email address. An access token might contain a user ID, but no PII.
• Refresh Tokens: Refresh tokens are only used to request new access tokens without forcing a user to reauthenticate. Remember, access tokens expire after a certain period. ID tokens are only generated when a user logs in and last until they log out.
Strategies for Using Access Tokens and Identity Tokens in Your Web Application
Now, let's examine how to leverage access tokens and ID tokens to boost the security of your web application. We focus on Duende IdentityServer, considering its high usability for ASP.NET Core apps. Many of these concepts also apply to other technology stacks.
Seamless support for OAuth 2.0 and OIDC remains a major advantage of using IdentityServer for ASP.NET Core applications. Software architects enjoy the ability to include industry-standard authentication and authorization services in their apps with ease. Restructuring an application design to leverage a security token service becomes simple as a result.
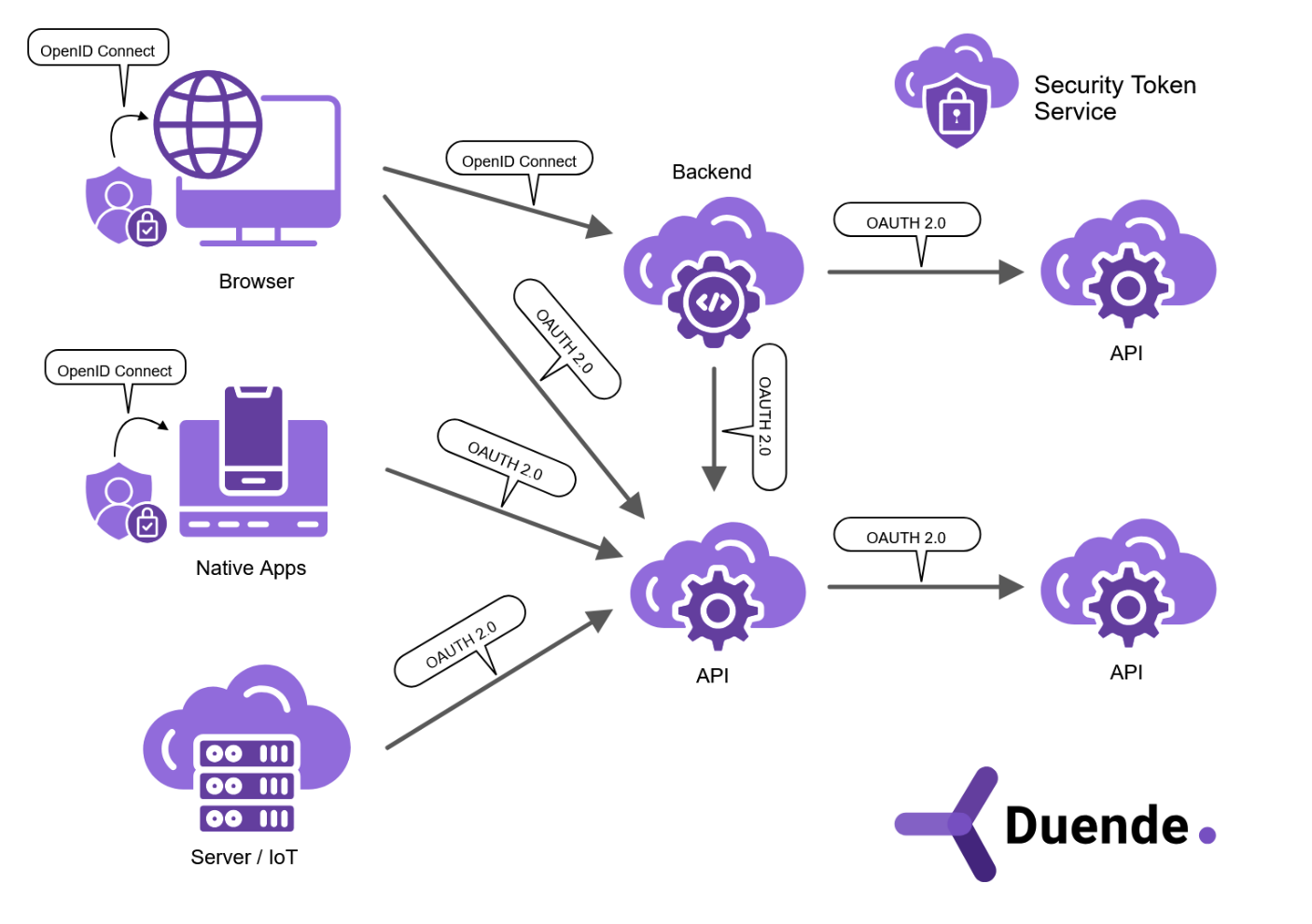
When a user logs in to an app, they use authentication functionality provided by OIDC, creating an ID token. Remember, that ID tokens aren't used to access an application's APIs. Instead, the app requests access tokens from the IdentityServer token service, following the OAuth 2.0 protocol. This approach provides a stronger security footprint for the application while also reducing its complexity.
Explore the application architecture in the above diagram, taken from The Big Picture in our documentation library. OpenID Connect uses an ID token when communicating with the Backend. OAuth 2.0 uses an access token when interacting with APIs. This diagram provides an easy way to visualize how developers answer the access token vs. ID token question.
Leveraging a standards-compliant security framework like IdentityServer offers a great option for securing your ASP.NET Core applications. IS supports the OAuth 2.0 and OpenID Connect specifications while you control your app's business logic and data. Partnering with Duende offers a great strategy for building and securing modern web and mobile applications. Connect with our helpful sales team to get your questions on Duende IdentityServer answered today.
