With .NET 10 just a few months away, November 2025 can’t come soon enough for developers looking to get their hands on the latest Long Term Support (LTS) release. What's new in .NET 10?
In this post, we’ll show and explain some of the latest auth-related features coming to .NET 10 and how they may positively impact your current Duende IdentityServer deployments. As we scoured the release notes, four enhancements caught our attention, and we thought you’d appreciate a detailed look at each new option.
ASP.NET Identity Passkey Support
Usernames and passwords have been an essential part of most authentication systems, and as developers, we’ve all built our fair share of systems secured by them. While passwords are the most commonly used option so far, developers have known that they are a less-than-ideal solution to secure modern systems. Recognizing that passwords are vulnerable to severe flaws, including leaks, weak passwords, and improper encryption use, the web standards community sought to develop a more secure approach.
In 2019, the World Wide Web Consortium (W3C) defined a set of APIs to help web developers build secure applications using digital signatures and cryptography. The specification is known as WebAuthn or FIDO 2.0, but developers commonly refer to it as passkeys. The first widely recognized implementation happened in 2022 by Apple, and since then, many vendors have implemented passkeys, including Google and Microsoft.
With the release of .NET 10, the ASP.NET team revisits the ASP.NET Identity library to add the passkeys feature and bring passwordless authentication support.
Duende IdentityServer supports ASP.NET Identity as a user store. Upgrading to the latest version of ASP.NET Identity and .NET 10 could help you implement passkeys as an authentication option for your users.
Read more in our series about passkeys - the future of authentication, including passkeys in .NET 10 Blazor apps with ASP.NET Identity. We’re very excited at the prospect of improved security for .NET developers.
Authentication and Authorization Metrics
Visibility into the security systems you build is essential in delivering a solution that finds the perfect balance between security and performance. Duende has gone through painstaking effort to add OpenTelemetry metrics into our IdentityServer offering, and we’re happy to see the ASP.NET Core team continue to add even more metrics. If anything is happening in your auth pipeline, then you’ll know about it.
To get started, you’ll need a tool that can monitor the latest metrics emitted from ASP.NET Core. For this post, we’ll use JetBrains Rider’s monitoring tool window. If you’re using Aspire, you can also look at our previous post on OpenTelemetry and Duende’s metrics and traces.
In JetBrains Rider, under the Monitoring tab, you’ll find the Counters and Metrics section. Add a new value of Microsoft.AspNetCore.Authentication to the Metric providers section.
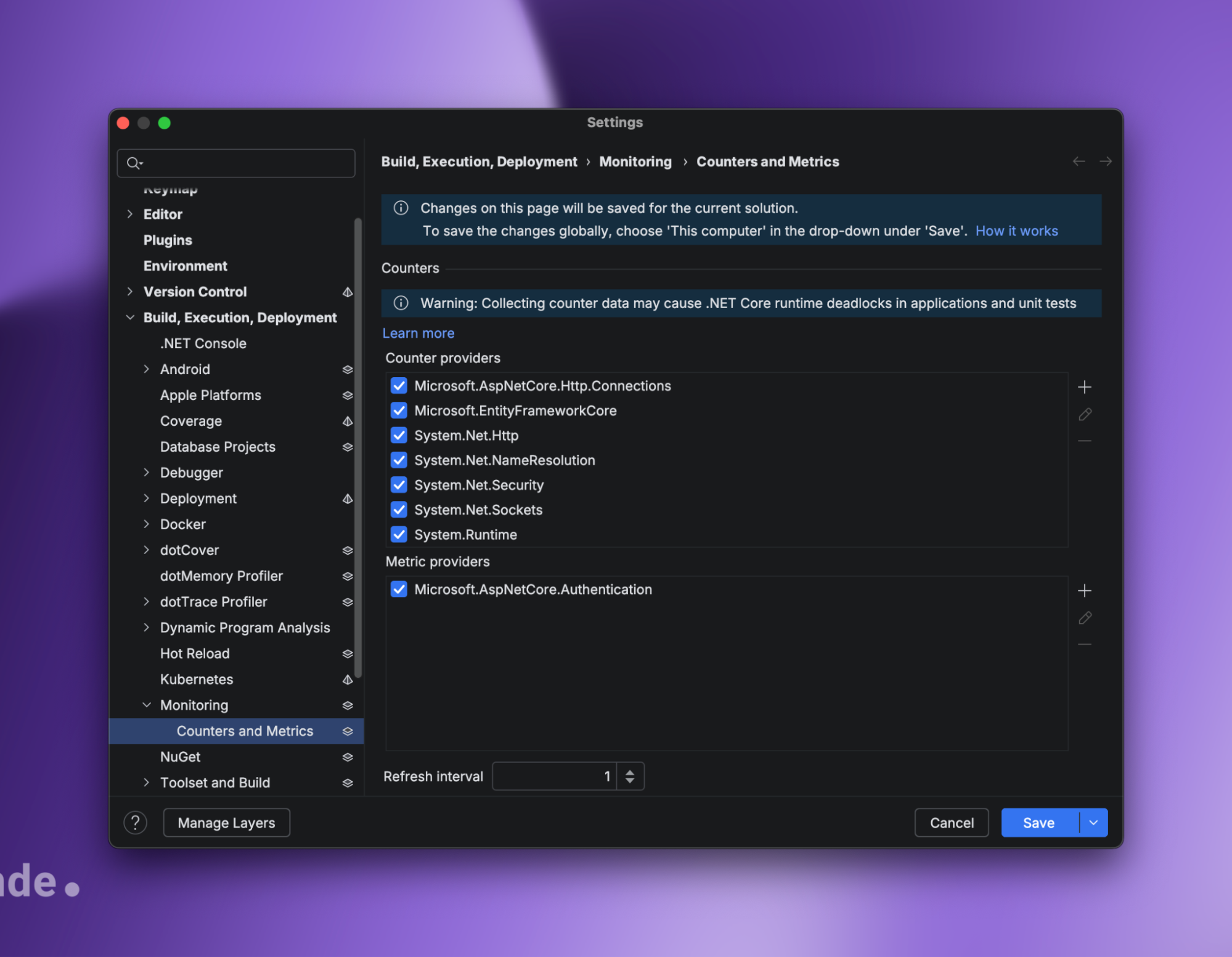
Once you’ve started your application, you’ll begin to see auth-related metrics in the Monitoring tool window under the Counters tab.
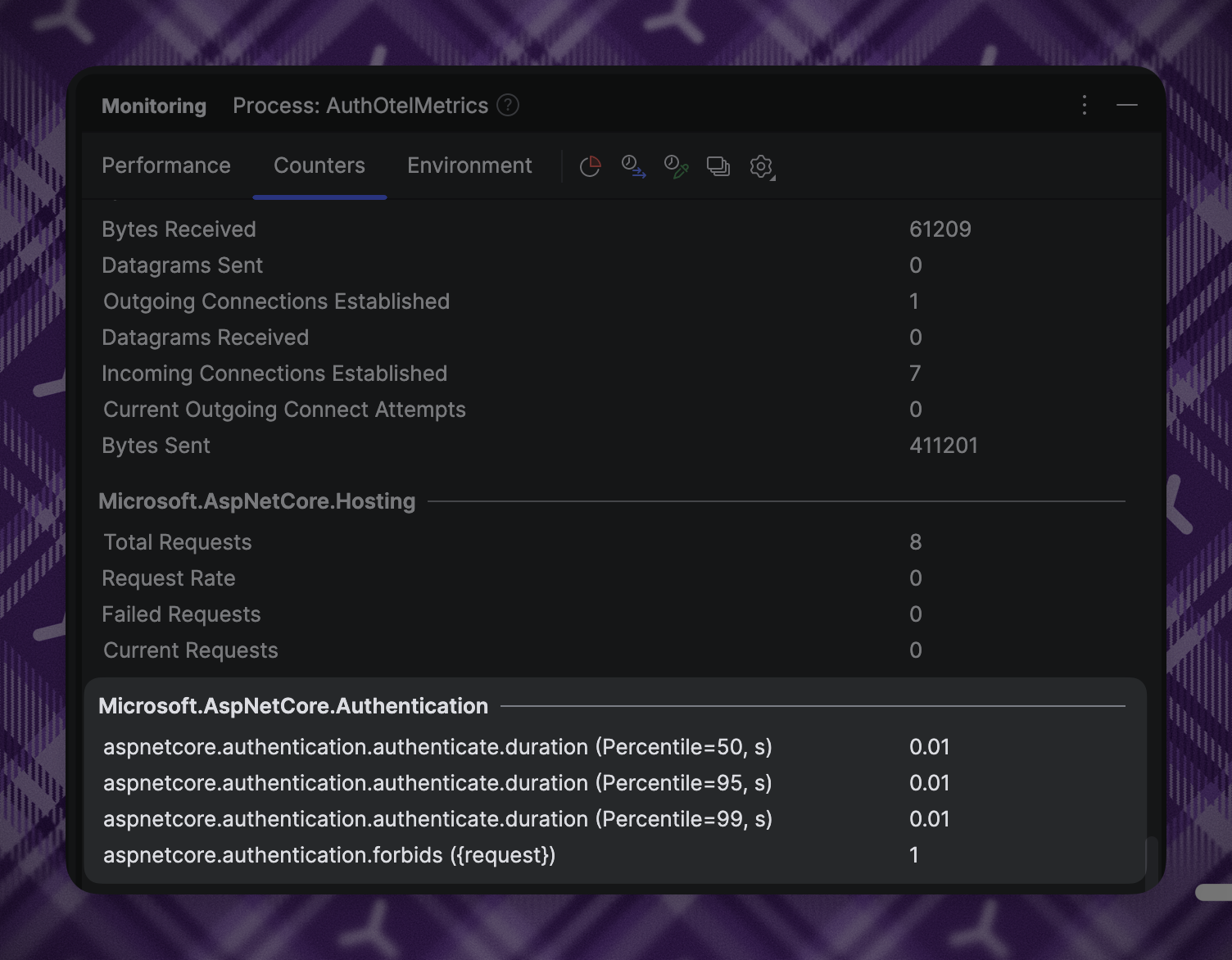
Note that ASP.NET Core logs messages with structured logging, which means there may be more information available than your current user interface is capable of displaying. Also, metrics are emitted and stored for the duration of the application’s runtime, so you will only see metrics that have occurred. You can expect to see the following metrics:
Authentication
- Authenticated request duration
- Challenge count
- Forbid count
- Sign-in count
- Sign-out count
Authorization
- Count of requests requiring authorization
These metrics can also be displayed in other tools such as Aspire’s dashboard or a Grafana dashboard, as shown below from the .NET 10 release notes.
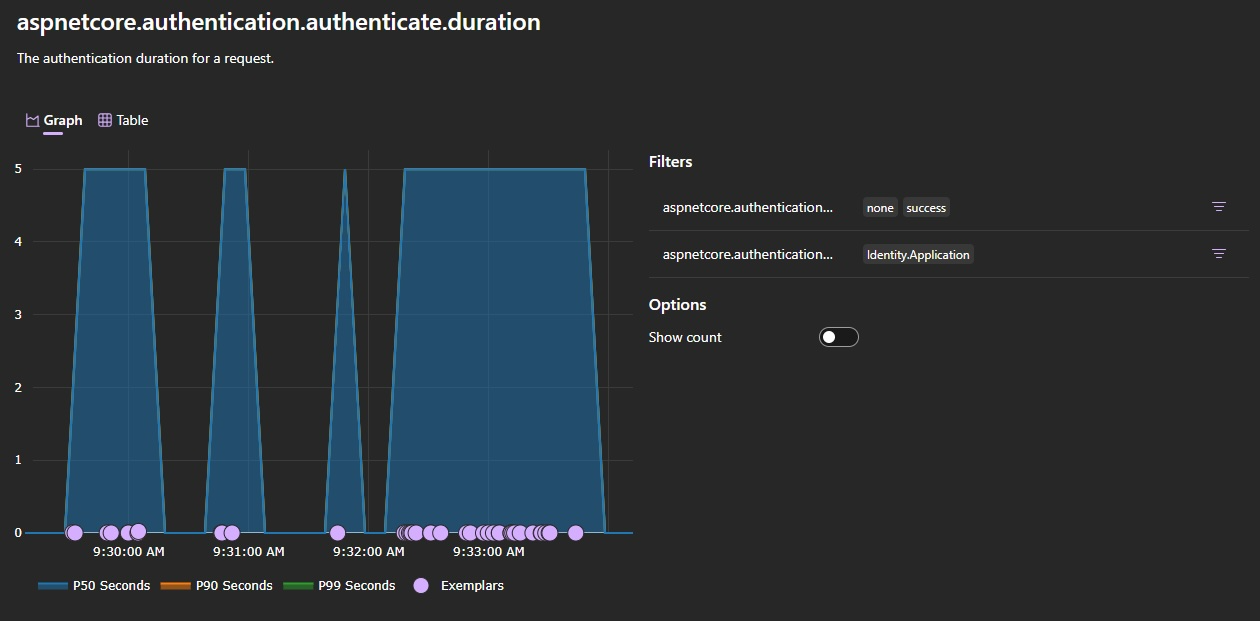
All said, this is an excellent feature for developers looking to understand their Duende IdentityServer deployments better and for those looking for the best operational efficiency they can squeeze out of existing hardware, all in service to delivering a fantastic user experience.
ASP.NET Core Identity metrics
Next to the authentication and authorization metrics, there are now also metrics for ASP.NET Identity. If you're using ASP.NET Identity as your IdentityServer user store, you'll be happy to learn you can now monitor key user and sign-in operation metrics. You can also track login attempts, sign-ins, sign-outs, and two-factor authentication usage.
The Microsoft.AspNetCore.Identity meter provides the following metrics:
User management metrics
- Duration of user creation operations (
aspnetcore.identity.user.create.duration) - Duration of user update operations (
aspnetcore.identity.user.update.duration) - Duration of user deletion operations (
aspnetcore.identity.user.delete.duration) - Number of password verification attempts (
aspnetcore.identity.user.check_password_attempts) - Number of tokens generated for users, such as password reset tokens (
aspnetcore.identity.user.generated_tokens) - Number of token verification attempts (
aspnetcore.identity.user.verify_token_attempts)
Authentication metrics
- Duration of authentication operations (
aspnetcore.identity.sign_in.authenticate.duration) - Number of password check attempts at sign-in (
aspnetcore.identity.sign_in.check_password_attempts) - Number of successful sign-ins (
aspnetcore.identity.sign_in.sign_ins) - Number of sign-outs (
aspnetcore.identity.sign_in.sign_outs) - Number of remembered two-factor authentication (2FA) clients (
aspnetcore.identity.sign_in.two_factor_clients_remembered) - Number of forgotten two-factor authentication (2FA) clients (
aspnetcore.identity.sign_in.two_factor_clients_forgotten)
CookieHandler Events
One of the dominant ASP.NET Core use cases is building APIs secured by OAuth, alongside hosting HTML-focused user interfaces. Hosting multiple authentication and authorization options in a single ASP.NET Core application can be challenging to implement correctly.
In .NET 10, the ASP.NET Core team changed the behavior of the Cookie authentication handler to avoid issues with incoming API requests. Moving forward, unauthenticated and unauthorized requests made to known API endpoints will result in a 401(Unauthorized) and 403 (Forbidden) status code, respectively, rather than redirecting what is likely a non-human client to a login URI.
ASP.NET Core identifies API endpoints by using the new IApiEndpointMetadata interface, and metadata implementing the new interface has been added automatically to the following:
[ApiController]endpoints- Minimal API endpoints that read JSON request bodies or write JSON responses
- Endpoints using
TypedResultsreturn types - SignalR endpoints
The change to the cookie handler logic is a transparent change to folks implementing Duende IdentityServer, as it shouldn’t have any direct impact on our implementation. For folks who are multi-hosting other functionality in their authorization server, you may want to be aware of this change and adapt accordingly.
Support for the .localhost top-level domain
In .NET 10, the ASP.NET Core development certificate has added the *.localhost and *.dev.localhost top-level domains as an option for resolving requests to a running ASP.NET Core application. As mentioned in the release notes, having this feature allows for better separation between local applications, as the client can now sandbox site assets based on unique names rather than accidentally sending local cookies to multiple ASP.NET Core applications.
For Duende IdentityServer developers, you can now create an experience more in line with a production environment without the headaches of additional containers, certificate management, or other headaches.
After installing the latest version of .NET 10 (currently RC 1), you should be able to install the newest certificate by executing the following command:
dotnet dev-certs https --trust
You can verify the certificate by looking in your operating system’s certificate store. Here’s a look at a macOS environment. Note that there are a few more DNS names; the additional names are to support Docker for Desktop and the Aspire development experience, but you can ignore those for now.
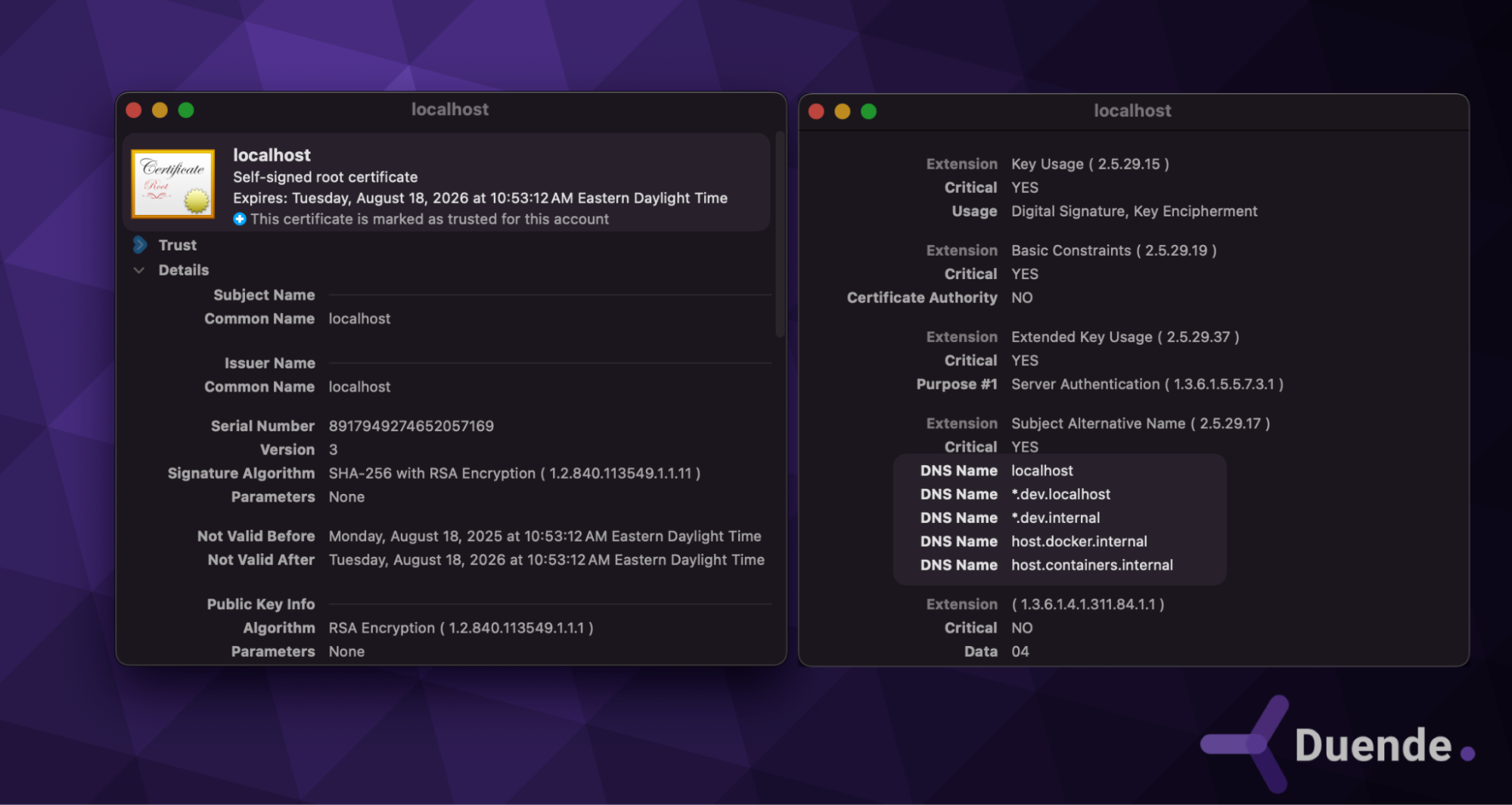
Once you’ve verified that you’ve installed the latest certificate, you can create a new Empty web application using the .NET template, and you may have to update your launchSettings.json file and the applicationUrl value.
{
"$schema": "https://json.schemastore.org/launchsettings.json",
"profiles": {
"http": {
"commandName": "Project",
"dotnetRunMessages": true,
"launchBrowser": true,
"applicationUrl": "http://WebApplication1.dev.localhost:5200",
"environmentVariables": {
"ASPNETCORE_ENVIRONMENT": "Development"
}
},
"https": {
"commandName": "Project",
"dotnetRunMessages": true,
"launchBrowser": true,
"applicationUrl": "https://WebApplication1.dev.localhost:7014;http://WebApplication1.localhost.dev:5200",
"environmentVariables": {
"ASPNETCORE_ENVIRONMENT": "Development"
}
}
}
}
After starting your application, you should see all the URLs your ASP.NET Core application is listening on in the console output.
info: Microsoft.Hosting.Lifetime[14]
Now listening on: https://WebApplication1.dev.localhost:7014
info: Microsoft.Hosting.Lifetime[14]
Now listening on: https://localhost:7014/
info: Microsoft.Hosting.Lifetime[14]
Now listening on: http://[::]:5200
info: Microsoft.Hosting.Lifetime[0]
Application started. Press Ctrl+C to shut down.
If you’re experiencing browser certificate trust issues, try quitting and restarting your current browser session.
Excited for .NET 10!
While there are certainly more features coming to .NET 10, the ones we’ve chosen for this post are likely the most impactful for our Duende community. From passkeys, metrics, cookie handler changes, and certificate improvements, the future for security on the .NET platform looks bright.
Let us know in the comments which .NET 10 features you’re most excited about, and if we’ve missed any we should be looking out for. As always, if you’re interested in Duende products, please feel free to check out our documentation site and engage with us in our GitHub community discussions.
